Raspberry Pi Remote Access: Easy Guide Behind Router
Is it possible to effortlessly control your Raspberry Pi from anywhere in the world, even when it's tucked behind a complex network of routers and firewalls? The answer is a resounding yes, and this guide will provide you with the roadmap to achieve this seemingly complex feat.
This exploration delves into the core principles of establishing secure remote access to your Raspberry Pi, meticulously detailing the necessary tools, configuration steps, and crucial security measures. Whether you're a seasoned developer or a curious beginner, this guide will serve as your comprehensive resource, paving the way for seamless remote control of your device.
The ability to manage and control your Raspberry Pi remotely unlocks a wealth of possibilities. Imagine the convenience of accessing your home automation system from your office, monitoring your weather station while on vacation, or remotely troubleshooting a project in the field. This capability extends far beyond mere convenience; it empowers you to monitor and maintain your devices, regardless of your physical location. This guide will furnish you with the knowledge to achieve this, simplifying the process and ensuring a secure and reliable connection.
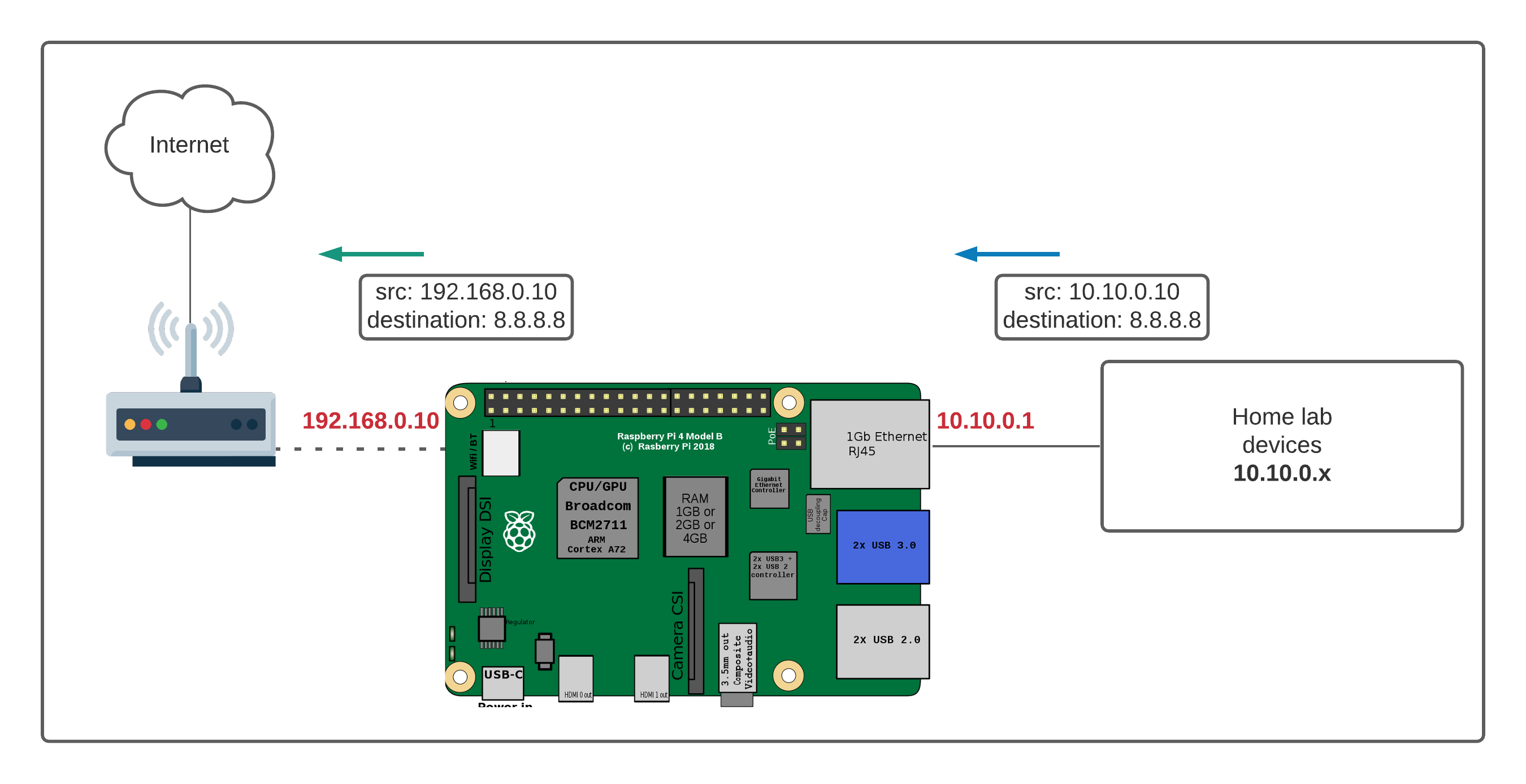
The challenge often lies in navigating the complexities of network configurations. Specifically, how do you access a device hidden behind a router, a device that often resides on a private network? This is where techniques such as port forwarding, VPNs, and cloud-based services come into play. These methods allow you to bypass the inherent limitations of your network setup, essentially creating a bridge to your Raspberry Pi from any location with an internet connection. Furthermore, the guide will also touch upon the complexities of corporate firewalls that might block standard ports like SSH or VNC connections, explaining how to circumvent such restrictions.
We'll dissect the most effective strategies, including setting up SSH and VNC connections, leveraging VPNs for secure access, and exploring cloud-based solutions like RealVNC's cloud VNC viewer. Additionally, the article touches upon simpler methods like using Raspberry Pi Connect, a free screen sharing and remote shell service, that can be a user-friendly alternative. The objective is to equip you with a comprehensive toolkit, empowering you to choose the method that best aligns with your needs and technical expertise.
One of the most powerful, yet straightforward, methods is utilizing Secure Shell (SSH). This technique provides a secure and encrypted channel for remote access, allowing you to execute commands, transfer files, and manage your Raspberry Pi's system directly from your remote location. Beyond SSH, the guide also examines using VNC (Virtual Network Computing) for visual access to your Raspberry Pi's desktop environment. VNC allows you to see and interact with the graphical interface, making it ideal for tasks that require a visual component.
But what happens when your Raspberry Pi resides behind a router or firewall? This is where techniques like port forwarding and reverse SSH tunnels become invaluable. Port forwarding, for example, allows you to route incoming traffic from a specific port on your router to your Raspberry Pi. However, this can be cumbersome and pose security risks if not implemented correctly. The guide will delve into the intricacies of port forwarding, offering practical tips and best practices.
Reverse SSH tunnels present an alternative, and in some cases, a more secure solution. This method establishes an outgoing connection from your Raspberry Pi to a remote server, allowing you to then connect to the Raspberry Pi through the remote server. This eliminates the need to open ports on your router, enhancing security and simplifying the configuration process.
Let's not overlook cloud-based solutions, which offer a simplified approach to remote access. Services like RealVNC provide a user-friendly interface, and often eliminate the need for complex network configurations. These services often handle the security aspects, allowing you to focus on using your Raspberry Pi.
Throughout this guide, the emphasis is on security. We'll cover crucial security measures, such as using strong passwords, enabling two-factor authentication, and keeping your system software up-to-date. We will emphasize that safeguarding your Raspberry Pi from unauthorized access is paramount. Failure to implement these measures can expose your device and your network to significant risks.
With the right approach, you can harness the full potential of your Raspberry Pi, enjoying the freedom and flexibility of remote access. The following sections will provide the step-by-step instructions and configuration details to help you to realize this. Whether youre looking for remote access for your home automation system or just want to learn a valuable new skill, we have you covered. The initial configuration might appear intricate, but rest assured that it is critical for establishing a secure and trustworthy remote connection. Consider that to begin this process, setting up the Raspberry Pi involves numerous steps.
Consider the network setup. Often, the Raspberry Pi is positioned behind a router. Moreover, you will need to know the external IP address provided by your modem. In this scenario, let's assume the modem's IP is 100.101.1.2. The local address for your Raspberry Pi is 192.168.1.100. If the goal is to target this host IP at 100.101.1.2, this connects to the network but doesn't specifically select the Raspberry Pi. As we explore this concept further, we will get into details about this.
To connect to a Raspberry Pi remotely, you can expose SSH or VNC on your Raspberry Pi over the open internet, within a VPN, or using an external service like RealVNCs cloud VNC viewer. You can also use Raspberry Pi Connect, a free screen sharing and remote shell service provided by Raspberry Pi.
The beauty of the system lies in the ability to directly SSH or VNC connect to the Raspberry Pi from anywhere as if it were on the local network. Moreover, remote connection can be made to an IoT device without needing to find the IoT device IP address and change any firewall settings. The simplicity of this lies in the fact you can directly connect to the Raspberry Pi behind a firewall from any place on the planet as if it was on the local network.
For many, the process of remote connection to a Raspberry Pi behind a router can seem daunting. But with the right steps and tools, it becomes a straightforward process. Connecting IoT devices remotely through a router using a Raspberry Pi has become a popular choice for hobbyists, professionals, and tech enthusiasts alike.
Here's a breakdown of the core steps that you can follow for a convenient connection. If you need to copy a file named myfile.txt from your personal computer to a users home folder on your Raspberry Pi, run the following command from the directory containing myfile.txt, replacing the placeholder with the username you use to log in to your Raspberry Pi and the placeholder with your Raspberry Pis IP address. With these in place, you can send commands and batch jobs to the Raspberry Pi from a web portal. This provides seamless remote access.
In practical terms, you might consider that you port forwarded 45000 for SSH. The steps will vary slightly depending on your router model, but the general process will involve logging into your router's administration interface, navigating to the port forwarding settings, and creating a rule that forwards traffic from the external port to your Raspberry Pi's internal IP address and port. While the setup might seem daunting at first, it is crucial to create a secure and reliable remote connection.
For those who want to bypass the intricacies of port forwarding, Tailscale presents an excellent option. Tailscale creates a private network between your devices using WireGuard, simplifying remote access. Installing Tailscale on your Raspberry Pi is a straightforward process. After installing, you will need to create an account. Then, the Tailscale interface will list all the devices registered under your account. Finally, you can access your Raspberry Pi from any of these devices.
Here is a table that provides some more insights:
| Feature | Description | Benefits | Considerations |
|---|---|---|---|
| SSH (Secure Shell) | A secure network protocol for operating network services securely over an unsecured network. |
|
|
| VNC (Virtual Network Computing) | A graphical desktop sharing system that uses the RFB (Remote Framebuffer) protocol to remotely control another computer. |
|
|
| VPN (Virtual Private Network) | A network that uses a public network (usually the Internet) to connect remote sites or users together. |
|
|
| Cloud-Based Services (e.g., RealVNC) | Services that handle the remote access setup, often offering a user-friendly interface. |
|
|
| Reverse SSH Tunnels | An SSH tunnel established from the remote device to a server that you control, allowing you to connect back to the device. |
|
|
| Tailscale | A mesh VPN that creates a private network between your devices using WireGuard. |
|
|