RemoteIoT: Secure IoT Device Management & Raspberry Pi Access
Can you truly manage your devices from anywhere, at any time? Remote access to your Internet of Things (IoT) devices isn't just a convenience; it's a necessity in today's interconnected world, offering unparalleled control and efficiency.
The evolution of technology has ushered in an era where devices are no longer confined to a specific physical space. From smart homes to industrial automation, the ability to remotely access and manage these devices is paramount. This capability, known as IoT remote access, empowers users to connect to, monitor, and control IoT devices from a remote location, eliminating the need for physical presence. It's a game-changer for industries that rely on real-time data, automated processes, and remote troubleshooting.
This transformation is driven by several factors, including the increasing adoption of IoT devices, the need for efficient device management, and the demand for enhanced security. The proliferation of IoT devices, from smart appliances to industrial sensors and connected vehicles, has created a vast network of interconnected systems that require constant monitoring and maintenance. The ability to remotely access these devices allows for proactive management, enabling users to diagnose and resolve issues before they escalate, minimizing downtime and maximizing productivity. Furthermore, IoT remote access provides a secure way to interact with devices, protecting critical data and systems from unauthorized access.
The benefits of IoT remote access are manifold, extending to various sectors. In the manufacturing industry, remote access allows for the monitoring of equipment performance, the detection of potential failures, and the optimization of production processes. In the healthcare sector, remote access facilitates the monitoring of patient vital signs, the remote management of medical devices, and the delivery of telehealth services. In the transportation industry, remote access enables the monitoring of vehicle performance, the remote diagnostics of issues, and the provision of over-the-air software updates. In essence, IoT remote access is transforming industries by providing greater control, efficiency, and security.
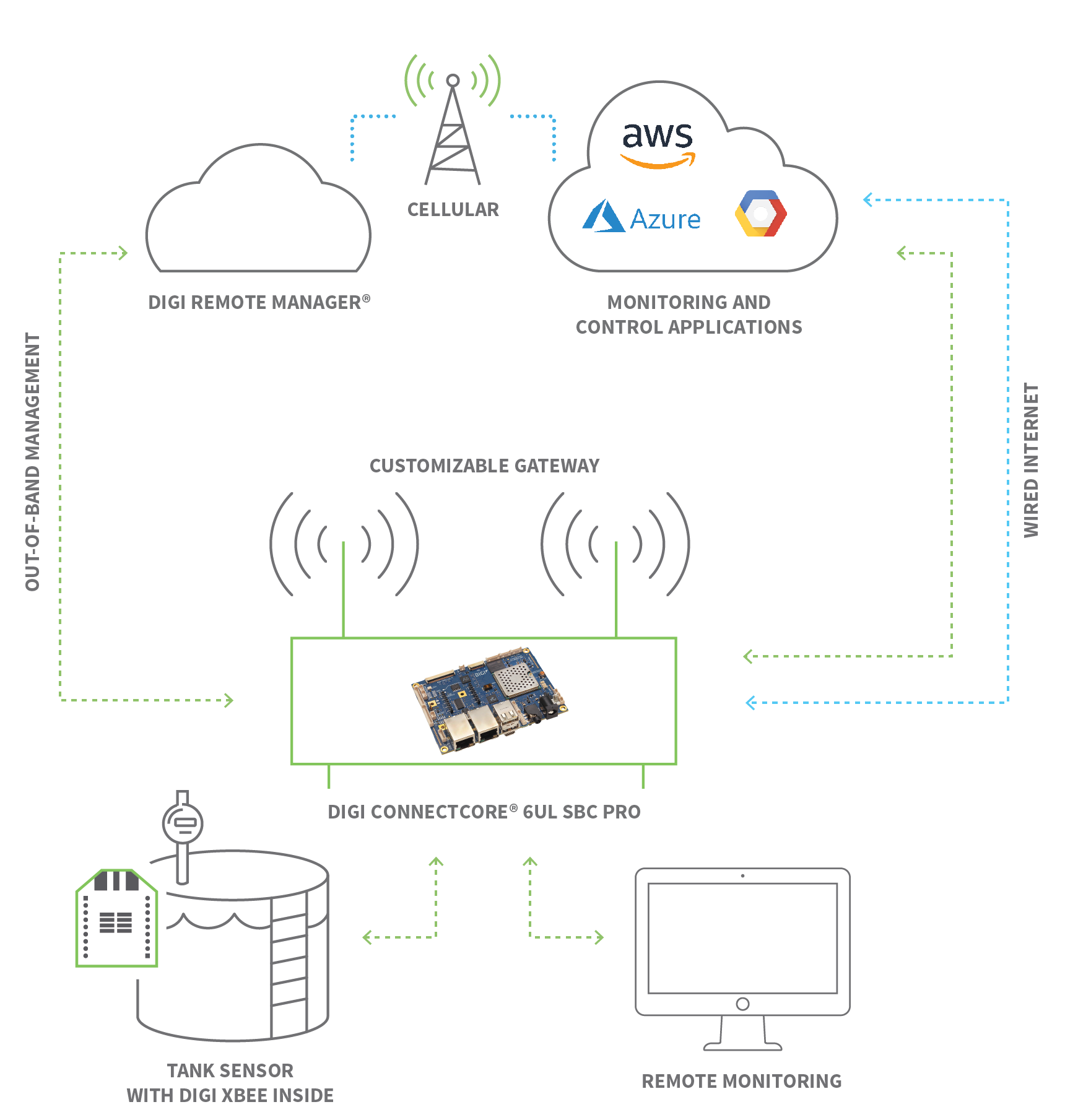
The architecture supporting this access can vary, but the underlying principles remain constant. Secure connections are paramount, often utilizing encrypted protocols like SSH to protect data transmitted over networks. Solutions like RemoteIoT leverage SSH tunneling to create secure pathways, even through firewalls, ensuring data integrity and privacy. This is a cornerstone of any robust IoT remote access implementation.
The process, while seemingly complex, is streamlined by modern tools. Let's delve into how a system like RemoteIoT simplifies the process for a popular IoT device: the Raspberry Pi. This pocket-sized computer is a favorite among enthusiasts and professionals alike, and remote access is a vital asset for its management.
The process usually involves the following steps. First, you'll need to install the remote access service on your Raspberry Pi. This typically involves accessing the device's terminal, either directly or via SSH on the local network, and running the necessary installation commands. Then, you'll open the remote access portal in your browser and log in to your account dashboard. Once logged in, you should see your Raspberry Pi listed among your account devices. From there, you can select the service you want to connect to and initiate the remote connection. Finally, you can use the provided connection information in applications like terminal, RDP, or a web browser. This creates a seamless, secure connection to your device.
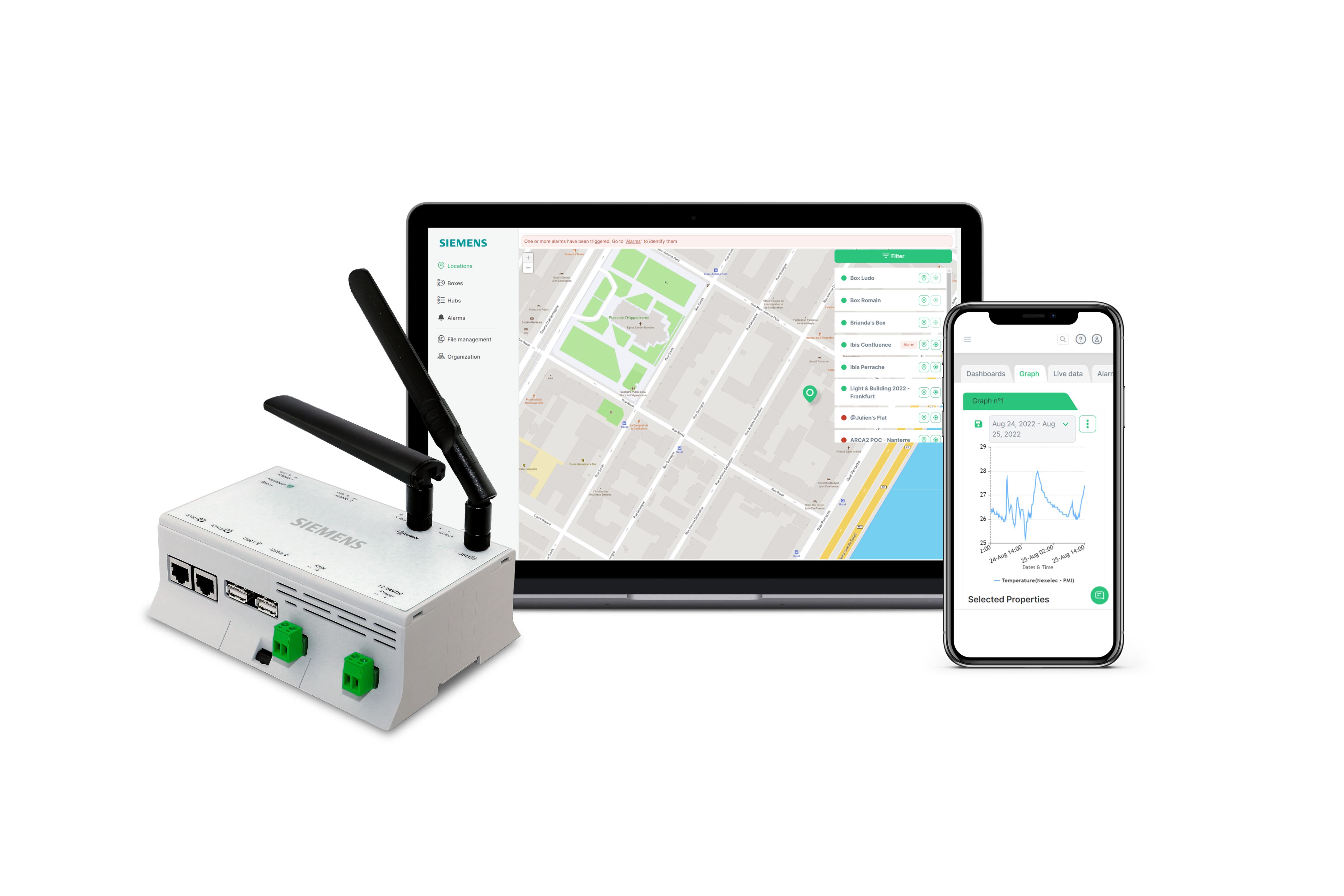
The power of RemoteIoT isn't just about convenience; its about enabling comprehensive control. The platform facilitates secure registration, organization, monitoring, and remote management of IoT devices at scale. You can monitor crucial system performance metrics, including device hardware data, CPU temperature, system error logs, and network performance data, all consolidated within a single, intuitive dashboard.
The benefits are vast, extending across diverse applications. Remote access ensures consistent monitoring, allowing for proactive issue resolution. Whether its troubleshooting a smart home appliance or managing an industrial sensor, remote access saves time and resources. Furthermore, it enhances security by enabling centralized control and monitoring, making your IoT infrastructure less vulnerable to unauthorized access.
One critical aspect of implementing such a system is understanding the security implications. The security landscape is constantly evolving, with new threats emerging regularly. Employing secure protocols, encryption, and authentication mechanisms is a must. Regularly updating software, monitoring for suspicious activity, and implementing robust access controls are essential to maintaining a secure environment.
For those seeking a more traditional approach, there are viable alternatives. Employing secure shell (SSH) protocol with a VPN or proxy connection is a common method, particularly for individuals not using AWS. SSH ensures encrypted connections, safeguarding critical commands and data. With the right configuration, this can provide secure remote access.
Let's examine the core concept: IoT Remote Access. Its the ability to connect to, monitor, and control your devices remotely. This is absolutely crucial for managing a broad spectrum of IoT devices, be they smart appliances, industrial sensors, or connected vehicles. Remote access eliminates the need to be physically present, enabling streamlined operations and maintenance.
Moreover, the accessibility of IoT remote access is expanding. Systems are being developed to work across a variety of internet connections, including Starlink, mobile, and CGNAT connections. The goal is to provide seamless access regardless of your location or the network infrastructure available.
Setting up an initial tunnel connection is usually achievable as long as the device can access the internet. For devices behind firewalls, solutions like RemoteIoT facilitate connectivity by using SSH tunneling. This encrypts all network traffic, ensuring secure communication. RemoteIoT VPC also gives you the ability to connect Raspberry Pi and IoT devices securely and directly from anywhere, as if they were on a local private network. You can even use it to logically group your devices or harden your public interface while allowing access from devices within the same virtual private cloud (VPC).
When deciding on a solution, consider what best suits your needs. Some platforms offer extensive features beyond mere screen sharing, including terminal access, application control, and edge management. These comprehensive solutions cater to complex IoT management scenarios.
Another useful application is the Arduino IoT Remote phone application, letting you control and monitor all of your dashboards in the Arduino Cloud. This is useful for mobile control, especially with access to your phone's internal sensors, such as GPS and light sensors. It can be an extremely useful tool depending on the specific requirements.
The mobile app, for example, may utilize both peer-to-peer (P2P) and proxy connections. Proxy connections, however, will have timeout rules consistent with the web portal. This ensures a balance between accessibility and security.
In the world of remote access, tools like RemoteIoT offer secure and efficient solutions. They can simplify your experience, and ultimately, provide a powerful solution for streamlining device management.
| Feature | Description | Benefits |
|---|---|---|
| Secure Connectivity | Utilizes SSH tunneling to encrypt all network traffic. | Ensures data privacy and security, even behind firewalls. |
| Centralized Management | Enables secure registration, organization, monitoring, and remote management of IoT devices at scale. | Simplifies device management, reduces operational overhead. |
| Comprehensive Monitoring | Provides a single dashboard to monitor system performance, device hardware metrics, CPU temperature, system error logs, and network performance data. | Enables proactive issue resolution, improves system uptime. |
| Versatile Access | Works over various connection types, including Starlink, mobile, and CGNAT connections. | Ensures remote access capabilities regardless of location or network infrastructure. |
| VPC Capabilities | Allows secure and direct connections to devices, as if they were on a local private network. | Enhances security and simplifies access management. |
Now, lets walk through the steps to set up remote access to your Raspberry Pi using a tool like RemoteIoT:
- Installation: Open the terminal of your Raspberry Pi (or access it via SSH on the local network) and install the RemoteIoT service using the appropriate command for your system.
- Dashboard Login: Once the service is installed, open the RemoteIoT portal in your browser and log in to your account dashboard.
- Device Verification: You should now see your Raspberry Pi listed in the list of account devices. If it isnt there, verify your installation and network configuration.
- Connection: Select the service you would like to create a RemoteIoT connection to and click connect.
- Application Use: Now, utilize the connection information in applications like terminal, RDP, Minecraft, Terraria, or a web browser to access your device remotely.
- Termination: When you're done with the connection, click "stop connection" to terminate the remote access session.
This process highlights how straightforward it is to begin managing your devices remotely.
To make the most of remote access, remember to implement the following security best practices:
- Use Strong Passwords: Protect your devices with unique, strong passwords.
- Regularly Update Software: Keep your system and all related software up to date.
- Monitor Network Traffic: Keep an eye on your network traffic for any unusual activity.
- Enable Two-Factor Authentication (2FA): Add an extra layer of security to protect your account.
- Use Encryption: Ensure that all data is transmitted securely, ideally using an encrypted protocol.
| Aspect | Details |
|---|---|
| Application | Raspberry Pi Management, Industrial Monitoring, Remote Diagnostics. |
| Key technologies | SSH Tunneling, Remote access portals, Mobile Applications. |
| Advantages | Secure connections, Easy Device Management, Remote Control capabilities. |
| Considerations | Network configurations, Security protocols, potential for downtime. |
The power of remote access lies in its flexibility. The tools are designed to integrate with a variety of platforms and services. To get the most out of remote access systems, understanding each service is key, as this is paramount to maximizing your control.
The final step can often be connecting to a server in a game like Terraria. After you have launched the game and clicked on multiplayer, you can "join via IP." You can then copy the hostname provided. This allows you to use remote connections in diverse and creative ways.
Many systems are now incorporating peer-to-peer (P2P) and proxy connections. When P2P is in use, expect quick connection times, higher data throughput, and heightened security. When a proxy connection is used, it will also timeout with the same rules as the web portal. This gives administrators a level of control that suits a wide range of needs.
Whether you are a technician or a homeowner, remote access offers benefits. From remote access software for a home PC to management software for industrial machinery, the potential is vast. It simplifies IT support, makes troubleshooting easier, and allows you to monitor processes without being physically present.
Remote access is not just a trend; it's a transformation. It redefines how we interact with devices, making them more accessible, manageable, and secure.